Emotional Footprint Awards 2024
Managed Detection & Response
SoftwareReviews names Field Effect MDR, Alert Logic MDR, Crowdstrike Falcon Platform, ReliaQuest GreyMatter, eSentire, and Kaspersky Managed Detection and Response as Managed Detection & Response Emotional Footprint Award Winners.
View Category
Managed Detection & Response
Emotional Footprint Awards
SoftwareReviews Emotional Footprint Awards evaluate and rank products based on emotional response ratings from IT and business professionals. Using our Emotional Footprint methodology, we aggregate emotional footprint scores across 26 dimensions of the vendor-client relationship and product effectiveness, creating a powerful indicator of overall user feeling toward the vendor and product.
Emotional Footprint Awards are proudly founded in 100% user review data and are free of traditional “magical” components such as market presence and analyst opinion, which are opaque in nature and may be influenced by vendor pressure, financial or otherwise.
Read The In-Depth Report
See how each vendor stacks up across each of the 26 dimensions and our thorough evaluation of vendor capabilities, product features, and overall satisfaction.
30+ pages

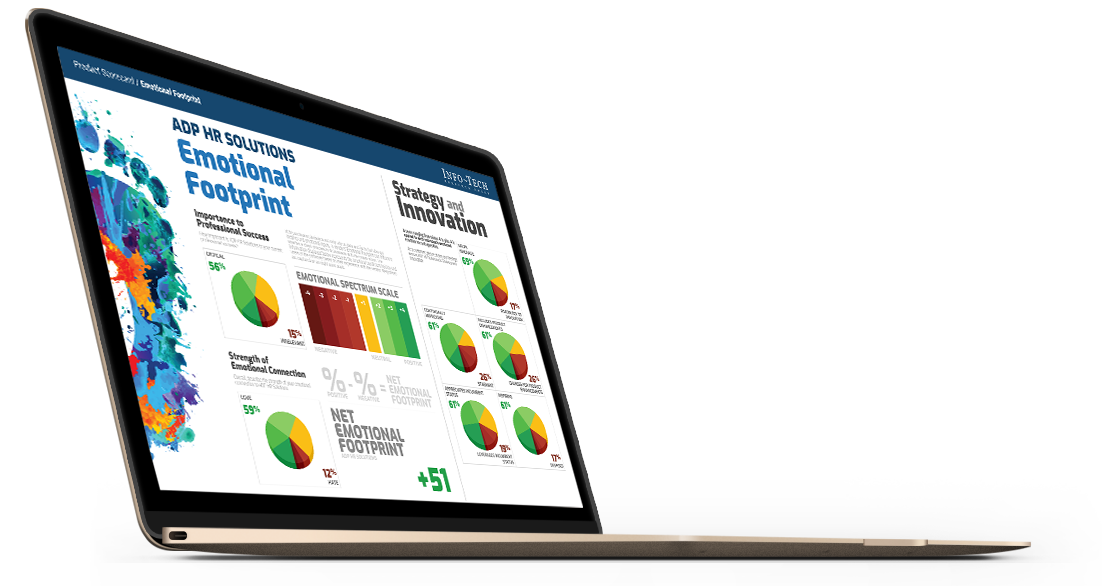
Measuring Emotional Footprint
Emotional Footprint is scored using our “Net Emotional Footprint” Index. This index tracks responses across 26 dimensions of emotional footprint that span 5 categories: Purchasing, Service Experience, Product Impact, Vendor Strategy, and Conflict Resolution. Then, the following calculation is done across this index:
% of Positive Reviews - % of Negative Reviews
For clarity, the total percentage of positive, neutral, and negative ratings is shown for each vendor as well.
Emotional Footprint Leaders
Field Effect
Field Effect MDR
Built from the ground-up to detect and respond to abnormal behaviour on endpoints, cloud services, and networks, Field Effect MDR (formerly Field Effect Covalence) is a holistic cyber security solution that delivers visibility into the threats and risks facing your business—giving you the advantages of automated cyber security, backed by human intelligence. No matter the size of your team or where they work, Field Effect MDR extends across your entire IT infrastructure. It pinpoints the cyber threats and vulnerabilities targeting your business and delivers the information you need to respond—all from one user-friendly platform.
9.6
CX Score
CX
Score
+100
Net Emotional Footprint
Net Emotional
Footprint
95
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.

38Reviews
Fortra
Alert Logic MDR
Cybersecurity attacks are on the rise. Alert Logic MDR® gives organizations the tools and expertise to detect, respond to, and eliminate security issues in their systems and networks.
9.3
CX Score
CX
Score
+97
Net Emotional Footprint
Net Emotional
Footprint
91
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.

32Reviews
Crowdstrike
Crowdstrike Falcon Platform
Detect, prevent and respond to attacks with next-generation endpoint protection delivered via the Falcon Platform.
8.8
CX Score
CX
Score
+92
Net Emotional Footprint
Net Emotional
Footprint
89
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.

28Reviews
ReliaQuest
ReliaQuest GreyMatter
ReliaQuest GreyMatter is a cloud-native security operations platform that helps organizations increase visibility, reduce complexity, and manage risk. Built on an open XDR architecture with bi-directional API integrations, GreyMatter enables security operations teams to extend detection, investigation, and response across multiple clouds, endpoint, and network infrastructures leveraging relevant data from both security and business applications.
8.7
CX Score
CX
Score
+97
Net Emotional Footprint
Net Emotional
Footprint
93
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.

11Reviews
eSentire
eSentire
eSentire is Managed Detection and Response, protecting your critical data and applications. It provides complete, multi-signal Managed Detection and Response providing 24/7 cutting-edge protection against cyber attackers that bypass traditional cybersecurity controls. eSentire MDR means high fidelity detection and unparalleled response. You shouldn’t settle for partial security, so we ingest multiple signals, correlating data across your network, endpoint, log, and cloud sources to disrupt threats before they impact your business.
8.6
CX Score
CX
Score
+98
Net Emotional Footprint
Net Emotional
Footprint
89
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.

17Reviews
Kaspersky
Kaspersky Managed Detection and Response
Kaspersky Managed Detection and Response (MDR) delivers advanced, round-the clock protection from the growing volume of threats circumventing automated security barriers, providing relief to organizations struggling to find specialized staff or with limited in-house resources.
8.5
CX Score
CX
Score
+97
Net Emotional Footprint
Net Emotional
Footprint
89
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.

10Reviews
Other Evaluated Vendors
Cynet
Cynet 360
The Cynet security platform correlates and analyzes indicators across all fronts of the organization – networks, files, users and endpoints – to establish risk-ranking and hone in on previously unidentified threats.
8.4
CX Score
CX
Score
+96
Net Emotional Footprint
Net Emotional
Footprint
88
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.
14Reviews
Red Canary
Red Canary MDR
Red Canary was founded to make security better. We defend hundreds of organizations around the world, with customers ranging from global Fortune 100s to 100-endpoint organizations. Our cloud-based MDR levels the playing field for businesses of all sizes by empowering your modern security operations center. to win against rapidly evolving adversaries.
8.1
CX Score
CX
Score
+90
Net Emotional Footprint
Net Emotional
Footprint
86
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.
15Reviews
Netsurion
Netsurion
Netsurion Managed XDR delivers both the technology and expertise you need to succeed. Our Open XDR platform unifies your existing security telemetry to deliver wider attack surface coverage and deeper threat analytics resulting in greater security visibility. Our SOC does the heavy lifting for you of proactive threat hunting, event correlation and analysis, and provides you with guided remediation. The result is a force multiplier that allows your IT team to be confident and in control again while also maximizing all of your cybersecurity investments.
7.8
CX Score
CX
Score
+84
Net Emotional Footprint
Net Emotional
Footprint
86
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.
16Reviews
Sophos
Sophos Managed Detection and Response
Sophos Managed Threat Response (MTR) provides 24/7 threat hunting, detection, and response capabilities delivered by an expert team as a fully-managed service. Built on our Intercept X Advanced with EDR technology, Sophos MTR fuses machine learning technology and expert analysis for improved threat hunting and detection, deeper investigation of alerts, and targeted actions to eliminate threats with speed and precision.
7.6
CX Score
CX
Score
+84
Net Emotional Footprint
Net Emotional
Footprint
78
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.
19Reviews
Rapid7
Rapid7 Managed Detection and Response
Rapid7 MDR is built from the ground up to help security teams of all sizes and experiences strengthen their security posture, find and stop attackers, and stay ahead of emerging threats. It is a combination of security expertise and leading technology solutions to detect dynamic threats quickly across your entire ecosystem to provide the hands-on, 24/7/365 monitoring, proactive threat hunting, effective response support, tailored security guidance, and team of Active Response experts to stop malicious activity and help you accelerate your security maturity.
7.4
CX Score
CX
Score
+80
Net Emotional Footprint
Net Emotional
Footprint
78
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.
15Reviews
Pillr
Pillr
A cybersecurity operations platform designed to take on the evolving demands of IT teams and service providers.
7.3
CX Score
CX
Score
+74
Net Emotional Footprint
Net Emotional
Footprint
83
Value Index
VALUE INDEX
Summary.
Long description.
Structure.
Chart graphic.
14Reviews
For the full list of vendors in this space, click here.
Download
Get Instant Access<br>to this Report
Get Instant Access
to this Report
Unlock your first report with just a business email. Register to access our entire library.
© 2025 SoftwareReviews.com. All rights reserved.


Contact Us
Welcome to SoftwareReviews!
Before continuing, please take a moment to review and agree to our policies and indicate your email preferences below:
Please sign in via LinkedIn to access your free .
Signing in also unlocks access to the dynamic version of the Data Quadrant, which plots vendors based on verified user reviews! Customize the Data Quadrant according to the features and sentiments that matter most to you.
Please note: the dynamic version of the Data Quadrant continues to collect data after report publication, and may show new data that will appear in next year's report.
This offer is available until May 31, 2020. These reports are intended for internal strategic use only and are not authorized for redistribution. For permission to reuse content, please contact vendors@softwarereviews.com.











