Home > Security Incident and Event Management
Customer Experience Awards 2019
Security Incident and Event Management
SoftwareReviews names Juniper Secure Analytics, ManageEngine Log360, Fortinet FortiSIEM, Splunk Enterprise Security, Graylog, and IBM QRadar as Security Incident and Event Management Customer Experience Award Winners.
View Category
Security Incident and Event Management
Customer Experience Awards
The SoftwareReviews Customer Experience Awards evaluate and rank products based on emotional response ratings from IT and business professionals. Our scoring methodology aggregates these ratings across 26 dimensions of the vendor-client relationship and product effectiveness, creating a powerful indicator of overall user feeling toward the vendor and product.
Customer Experience Awards are proudly founded in 100% user review data and are free of traditional “magical” components such as market presence and analyst opinion, which are opaque in nature and may be influenced by vendor pressure, financial or otherwise.
Read The In-Depth Report
See how each vendor stacks up across each of the 26 emotional response areas, and how they compare against each other. Our Customer Experience Report covers all aspects of the vendor-client relationship.
30+ pages
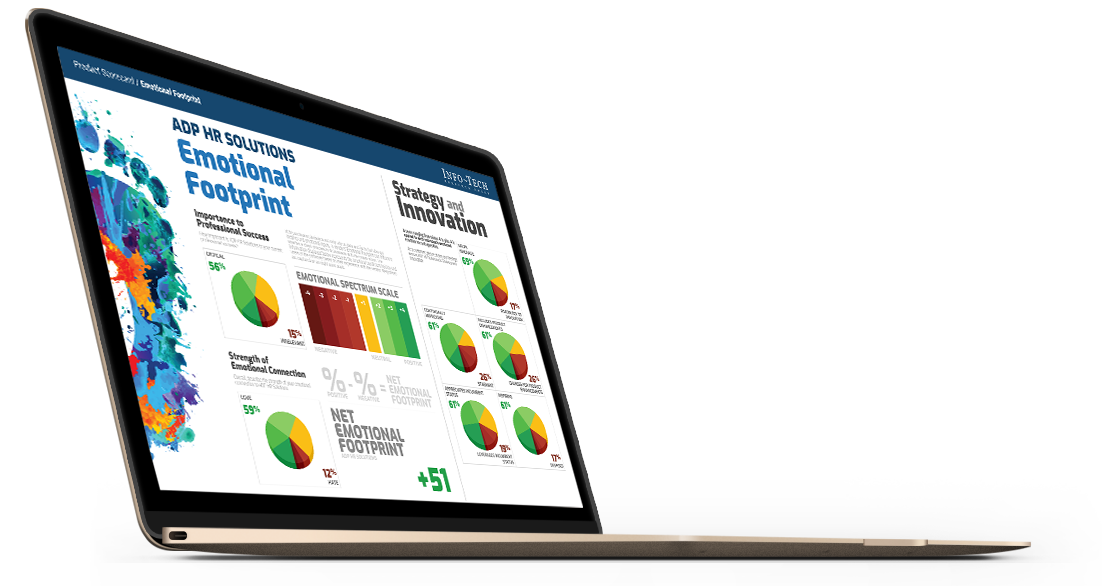
Measuring Customer Experience
Customer Experience Award rankings are scored using our “Net Emotional Footprint" index, which tracks responses across 26 emotional response areas that span 5 categories: Purchasing, Service Experience, Product Impact, Vendor Strategy, and Conflict Resolution. The following calculation is done across this index:
% of Positive Reviews - % of Negative Reviews
For clarity, the total percentage of positive, neutral, and negative ratings is shown for each vendor as well.
Customer Experience Leaders
Juniper Networks
Juniper Secure Analytics
Market-leading security information and event management (SIEM) that consolidates large volumes of event data from thousands of Juniper and non-Juniper devices, endpoints, and applications in near real time.
+90
Net Emotional Footprint
Net Emotional
Footprint
Strongest
Positive Emotions
100% Friendly Negotiation
100% Respectful
100% Fair
Summary.
Long description.
Structure.
Chart graphic.

11Reviews
ManageEngine
ManageEngine Log360
ManageEngine Log360 is a one-stop comprehensive SIEM solution for all your log management and network security challenges. Defend against internal and external attacks with real-time log collection, analysis, correlation and archiving capabilities.
+89
Net Emotional Footprint
Net Emotional
Footprint
Strongest
Positive Emotions
100% Effective
100% Saves Time
100% Reliable
Summary.
Long description.
Structure.
Chart graphic.

14Reviews
Fortinet
Fortinet FortiSIEM
FortiAnalyzer Network Security Logging, Analysis, and Reporting Appliances securely aggregate log data from Fortinet Security Appliances. A comprehensive suite of easily customable reports allows you to quickly analyze and visualize network threats, inefficiencies and usage.
+88
Net Emotional Footprint
Net Emotional
Footprint
Strongest
Positive Emotions
100% Efficient
100% Performance Enhancing
100% Includes Product Enhancements
Summary.
Long description.
Structure.
Chart graphic.

21Reviews
Splunk
Splunk Enterprise Security
Splunk Enterprise makes it simple to collect, analyze and act upon the untapped value of the big data generated by your technology infrastructure, security systems and business applications—giving you the insights to drive operational performance and business results.
+87
Net Emotional Footprint
Net Emotional
Footprint
Strongest
Positive Emotions
96% Fair
95% Reliable
95% Unique Features
Summary.
Long description.
Structure.
Chart graphic.

57Reviews
Graylog
Graylog
Graylog is an open source log management that actually works. Centralize and aggregate all your log files for 100% visibility. Use our powerful query language to search through terabytes of log data to discover and analyze important information.
+86
Net Emotional Footprint
Net Emotional
Footprint
Strongest
Positive Emotions
100% Efficient
96% Effective
96% Fair
Summary.
Long description.
Structure.
Chart graphic.

30Reviews
IBM
IBM QRadar
IBM® Security QRadar® SIEM consolidates log source event data from thousands of devices endpoints and applications distributed throughout a network. It performs immediate normalization and correlation activities on raw data to distinguish real threats from false positives.
+84
Net Emotional Footprint
Net Emotional
Footprint
Strongest
Positive Emotions
96% Respectful
93% Enables Productivity
91% Efficient
Summary.
Long description.
Structure.
Chart graphic.

47Reviews
Other Evaluated Vendors
AT&T Cybersecurity
AT&T Cybersecurity SIEM Solutions
We founded AT&T Cybersecurity to help organizations of all shapes and sizes achieve world-class security without the headaches and huge expense of other solutions. And we are passionate about our mission.
+79
Net Emotional Footprint
Net Emotional
Footprint
Strongest
Positive Emotions
100% Integrity
100% Enables Productivity
100% Reliable
Summary.
Long description.
Structure.
Chart graphic.
12Reviews
LogRhythm
LogRhythm Security Intelligence Platform
You need deep, real-time visibility into your entire IT environment to defend your organization from today’s threats. LogRhythm analyzes all of your forensic data. It fills gaps with endpoint and network sensors. With LogRhythm, you get the intelligence and tools you need to protect your network.
+78
Net Emotional Footprint
Net Emotional
Footprint
Strongest
Positive Emotions
94% Effective
94% Respectful
88% Caring
Summary.
Long description.
Structure.
Chart graphic.
17Reviews
Intel Corporation
McAfee Enterprise Security Manager
As the foundation of our security information and event management (SIEM) solution, McAfee Enterprise Security Manager delivers the performance, actionable intelligence, and real-time situational awareness required for organizations to identify, understand, and respond to stealthy threats, while the embedded compliance framework simplifies compliance.
+75
Net Emotional Footprint
Net Emotional
Footprint
Strongest
Positive Emotions
90% Respectful
87% Integrity
86% Reliable
Summary.
Long description.
Structure.
Chart graphic.
173Reviews
SolarWinds
SolarWinds SIEM: Log and Event Manager
Find attacks and demonstrate compliance immediately. Receive actionable data in less time with a turnkey SIEM. Log & Event Manager is an all-in-one solution deployed as a hardened virtual appliance with built-in rules, filters, and reports.
+75
Net Emotional Footprint
Net Emotional
Footprint
Strongest
Positive Emotions
91% Respectful
89% Saves Time
88% Helps Innovate
Summary.
Long description.
Structure.
Chart graphic.
35Reviews
Dell
Dell Quest InTrust
InTrust enables you to securely collect, store, search and analyze massive amounts of IT data from numerous data sources, systems and devices in one place. Get real-time insights into user activity for security, compliance and operational visibility.
+66
Net Emotional Footprint
Net Emotional
Footprint
Strongest
Positive Emotions
95% Integrity
84% Unique Features
84% Caring
Summary.
Long description.
Structure.
Chart graphic.
19Reviews
For the full press release, click here. For the full list of vendors in this space, click here.
Download
Get Instant Access<br>to this Report
Get Instant Access
to this Report
Unlock your first report with just a business email. Register to access our entire library.
© 2025 SoftwareReviews.com. All rights reserved.


Contact Us
Welcome to SoftwareReviews!
Before continuing, please take a moment to review and agree to our policies and indicate your email preferences below:
Please sign in via LinkedIn to access your free .
Signing in also unlocks access to the dynamic version of the Data Quadrant, which plots vendors based on verified user reviews! Customize the Data Quadrant according to the features and sentiments that matter most to you.
Please note: the dynamic version of the Data Quadrant continues to collect data after report publication, and may show new data that will appear in next year's report.
This offer is available until May 31, 2020. These reports are intended for internal strategic use only and are not authorized for redistribution. For permission to reuse content, please contact vendors@softwarereviews.com.










